|
-- The authentication
In this section we will examine how to create the authentication by using asymmetric cryptography.
.
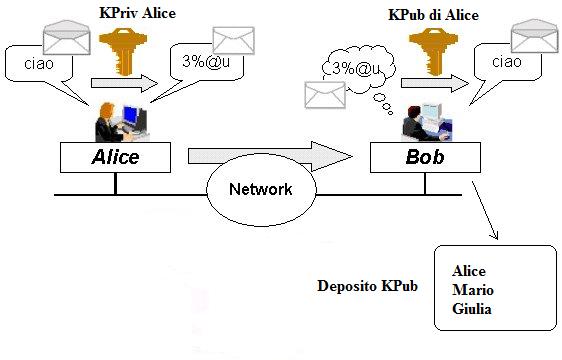
Let’s suppose I want to be sure that the person who receives my message knows that I am the real sender and there and no one else could create it by using my signature. The authentication by asymmetric key is at the base of the so called digital signature. How does it work? I keep my secret(my document) locked with my private key in a box. Since I only have the private key I am the only person who can close the box. Now I send my box around the world. Who can open my box? Only those who have my public key. This means only the person I gave my key to. I’ll give an example: Bob owns more than one key (Alice’s key, Mario’s key, Giulia’s key) and he tries to open the box which has been locked with Alice’s private key. If he uses Mario’s public key the safety lock does not open. If he uses Giulia’s one it does not open as well. Since the box was locked with Alice’s private key, if he uses that one it works. So, if Bob is able to open the lock by using Alice’s public key this means that the box had been closed with Alice’s private key. However, since Alice’s private key is owned only by her, this means that that box can only come from Alice. The authentication is obviously part(the first part) of the cryptography process with asymmetric key.
 12/27
12/27

|