Secret key algorithms provide the use of the same key for both the codification and decodification of the code.
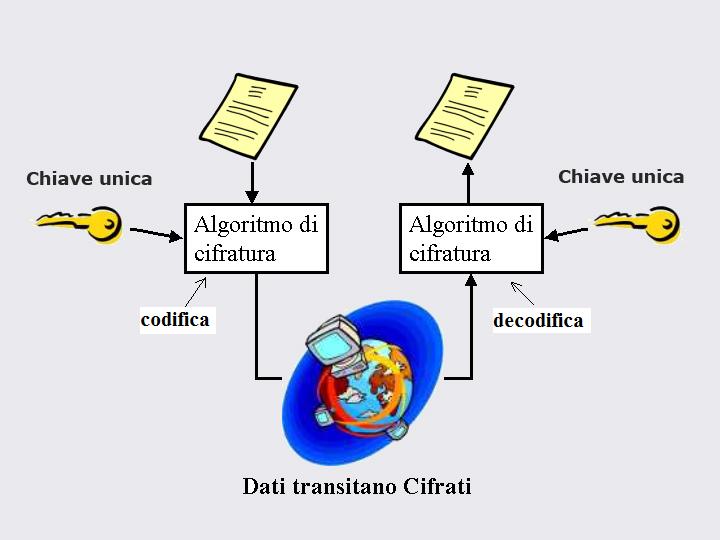
The key is said to be symmetric because as you can see there is an axis of symmetry that forces me to use this key both to shift from the original text to coded text and vice-versa. The problem is that this key needs to be secret. Actually if we refer to Cesar epoque that key has to be known by Cesar and his generals and no one else, otherwise the person who comes into possession of this key can decode the message and compromise its secrecy.
The main problem of algorithms with symmetric key [I1] [I2] [F1]
[F2] [S1] [S2] [E1] [E2] is the safe and wide distribution of keys. The entire safety of the algorithm is based on the secrecy of the key that has to be known only by the two interlocutors. For this reason we usually prefer a physical delivery of the key rather than sending it on a communication channel. However sometimes the exchange can take a bit of time. This means that the private key will stay unchanged for a long time, making more easy for people to break the code.
There are different algorithms that allow this type of cryptography. Here you can find some of them.
- DES
- TRIPLO DES
- IDEA
- RC2, RC4, RC5
- AES
- CAMELLIA
These are names often used, especially for e-commerce or when coding a file by using performances offered by a system of secret file management.