Computer viruses [I1] [I2] [I3][I4] [F1] [F2] [F3]
[F4]
[F5] [S1] [S2] [S3] [E1]
[E2] are basically hidden programmes, that is, a part of the code inside a programme or file that by using them is able to spread from a computer to another. Unlike the Trojan horse, as you can see from the picture, the virus duplicates itself autonomously and at a certain point, if there are specific conditions, it is automatically executed without we realize and causing damages that can be very serious.
The concept of virus is represented in the following scheme:
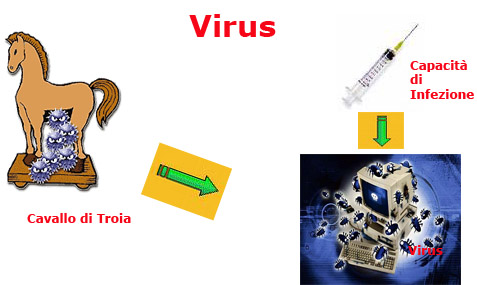
The concept of a Trojan (a hidden programme) is linked with the ability to infect other programmes. This ability to infect causes a spreading phenomenon that can be extremely fast and virulent.
Viruses can be more or less dangerous for the operating system that hosts them; however even if not so dangerous they can waste a big portion of RAM, CPU and space on the hard disk.
The general rule is that a virus can damage directly only the software of the hosting computer even if indirectly it can damage also the hardware, for example by causing CPU overheating through overclocking or by stopping the cooling fan.
Virus is often a synonymous of malware, to refer to different "infenstant" categories, such as worms, trojan horses, or dialer.
A virus is made of different instructions just like any other computer programmes. It usually has a small number of instructions, few bites and some kilobytes. The main feature of the virus is that of reproducing and spreading inside the PC any time you open the infected file.
A virus is not a programme you can execute, just like a biological virus is not a life form. A virus needs the human action to be activated.
There are two moments for a virus:
-
when the virus is present only on the mass support (hard disk, floppy, CD..) the virus is inactive and is not able to do anything unless the programme that hosts it is executed;
-
when the virus is uploaded on the RAM memory it becomes active.
Usually a virus copies itself spreading the epidemic but it can have more dangerous tasks (cancel or ruin files, format the hard disk, open back doors, show up messages, drawings or modify the aspect of the screen).
Some particular viruses are the macro [I1] viruses; they are usually inside a Microsoft Word, Microsoft Excel o Microsoft PowerPoint documents and consist in a macro.
For example, if a Word document contains a Macro with a virus, once you open the document and execute the Macro, you will execute also the virus that it contains.
The virus will be able to:
• perform destructive actions (es. write over one or more files cancelling them)
• riproduce itself (to modify style sheets, to copy itself on other documents)
• to modify Word menus changing name and meaning to operations
A way to fight macro viruses is to set a high (to execute only Macros with safe digital signature) or medium (that requires the confirmation) protection for Macros.
With the introduction of nets, viruses have changed features, not in the basic concepts or objectives, but in the spreading mechanisms among systems. Once viruses used to spread passing from a floppy disk to another; today PCs are connected on the net and viruses have turned into worms.
Worms [I1] use the net and interconnections as instruments to spread. And the name comes from that: a worm is something that moves underground deviously, in this case on the net.
Worms have often involved many PCs and performed very serious phenomena often destructive in very short time.
Unlike a “classic” virus, the worm does not need to link itself to other programmes to spread.
Usually it modifies the starting software of the PC he wants to infect so that it is executed any time you switch on the computer and stays on until you switch it off or the corresponding process stops. The worm tries to duplicate itself using internet in different ways:
• e-mail: the worm searches for memorized addresses on the PC and sends a copy of itself as an attachment to all of them it could collect.
• file sharing: the worm copy itself among the shared files of the victim, pretending to be an ambitious programme or a crack of very expensive and rare programmes to induce other users to download and execute it.
In this animated picture we want to show you how the famous Red code worm spread very briefly infecting thousands of computers of the whole world.

It is extremely important to see how, in few seconds of simulation, the world was infected compromising the whole connection system which is extremely complicated, difficult but very fragile in these kind of cracking phenomena