There are different types of menaces. We tried to sum them up trying to use some very common terms also known through the mass media.
The different types of menaces [I1] [I2]
[I3]
[F1] [S1] [S2] [S3] [E1] can be classified in different categories. Some of them will be studied in more details.
We will talk about unlawful intrusion on nets referring to what is widely known as Hacker Intrusion. This action is realised through the so called malware, that is, a software created with the only aim of causing damages on the computer on which it is used.
The word comes from the english words “malicious” and “software” and litteraly means “malicious software”. It Italian is also said malicious code.
In the next pages of this hypertext we wil point our attention on the main typologies of malware focusing on viruses and net viruses (worms), but also on the irritating phenomenon of spamming which is the inappropriate e-mail diffusion. We will then talk about spyware, that is, those software that try to look inside our computer without let us realize. Then we will analyse the social phenomenon of phishing and the troian horse which is the technology at the basis of all these menaces.
Before analysing in details the different types of menaces it is interesting to see how they are distributed. In the following picture you will see a division of the types of menaces that affect processing systems and net systems.
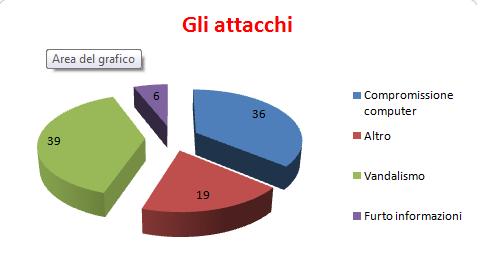
As you can see menaces have different aims. 35% of them aims at damaging systems to make them not work properly. Another big percentage aims at computer science vandalism as for example to block entering an e-commerce web site. Finally we can find information theft since nowadays they are all digitally codified inside the hard disk and the systems. Once upon a time dossiers were stolen, today files.